Stop fraud before it starts

Spot suspicious patterns, prevent fraud
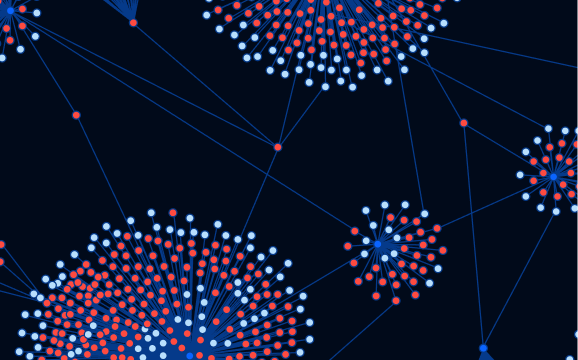
Bad actors change tactics, but the devices, locations, and items they use stay the same. We’ve seen unrelated applications across Truepic customers trace back to the same device.
The Truepic Risk Network surfaces devices tied to suspicious activity across participating customers, helping you detect fraud sooner.
benefits

Catch fraud earlier

Reduce losses

Share intelligence
Understand suspicious activity
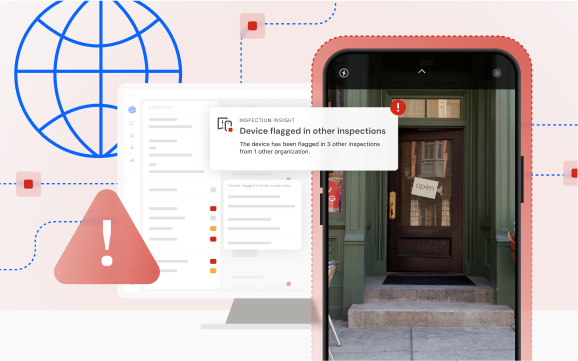
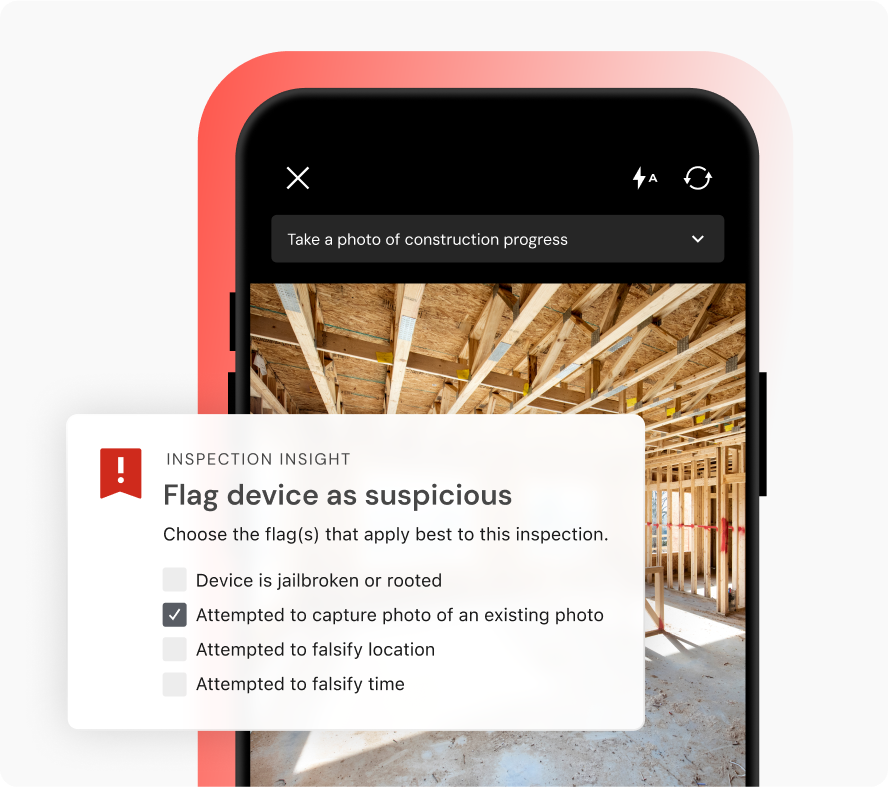
Truepic Vision will now flag an inspection if:
The device is jailbroken or rooted: indicates attempts to bypass system protections
The device is falsifying its location: reveals GPS spoofing or location-mocking tactics
Multiple devices were used: reveals unusual inspection activity to prioritize for deeper review
Same device found in multiple inspections: highlights inspections that may involve the same bad actor
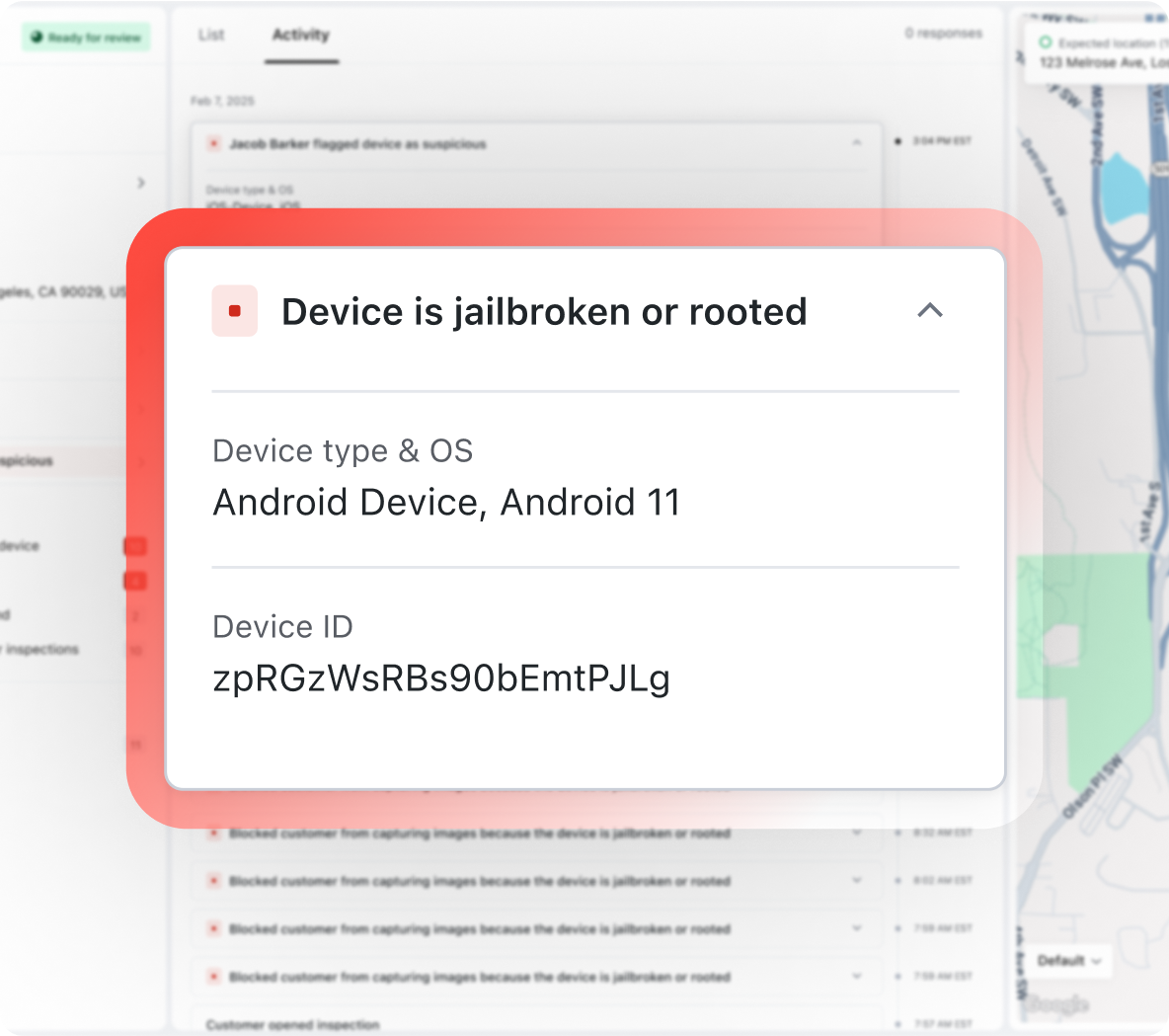
Track suspicious devices
Tag devices based on suspicious inspection content
Share device flags and rationale across your organization
Access shared intelligence
Get real-time alerts when an inspection was previously flagged as suspicious by another participant in the network
Includes information about why the inspection associated with the device was marked suspicious
Powered by an opt-in consortium of customers with anonymized data
All members are required to report data on a continuous basis

Additional Resources
Learn more about how Truepic detects and prevents fraud
Join the COMMUNITY