TRUEPIC BLOG
Why you need to understand Visual Risk today

Authored by Jeffrey McGregor, CEO of Truepic
Our world is digital. The benefits of efficiency, convenience, connectivity, and speed are unmatched when compared to human-centric processes. Nearly every aspect of life, and especially the economy, has been digitized, from lending and audits to inspections, onboarding, financial transactions, and more. This paradigm shift will continue to guide growth and innovation for years to come, but it is important for business leaders to understand that these changes introduce significant challenges in the form of visual risk.
What is visual risk?
Visual risk refers to the threats and vulnerabilities in digital visual imagery that can enable fraud and deception.
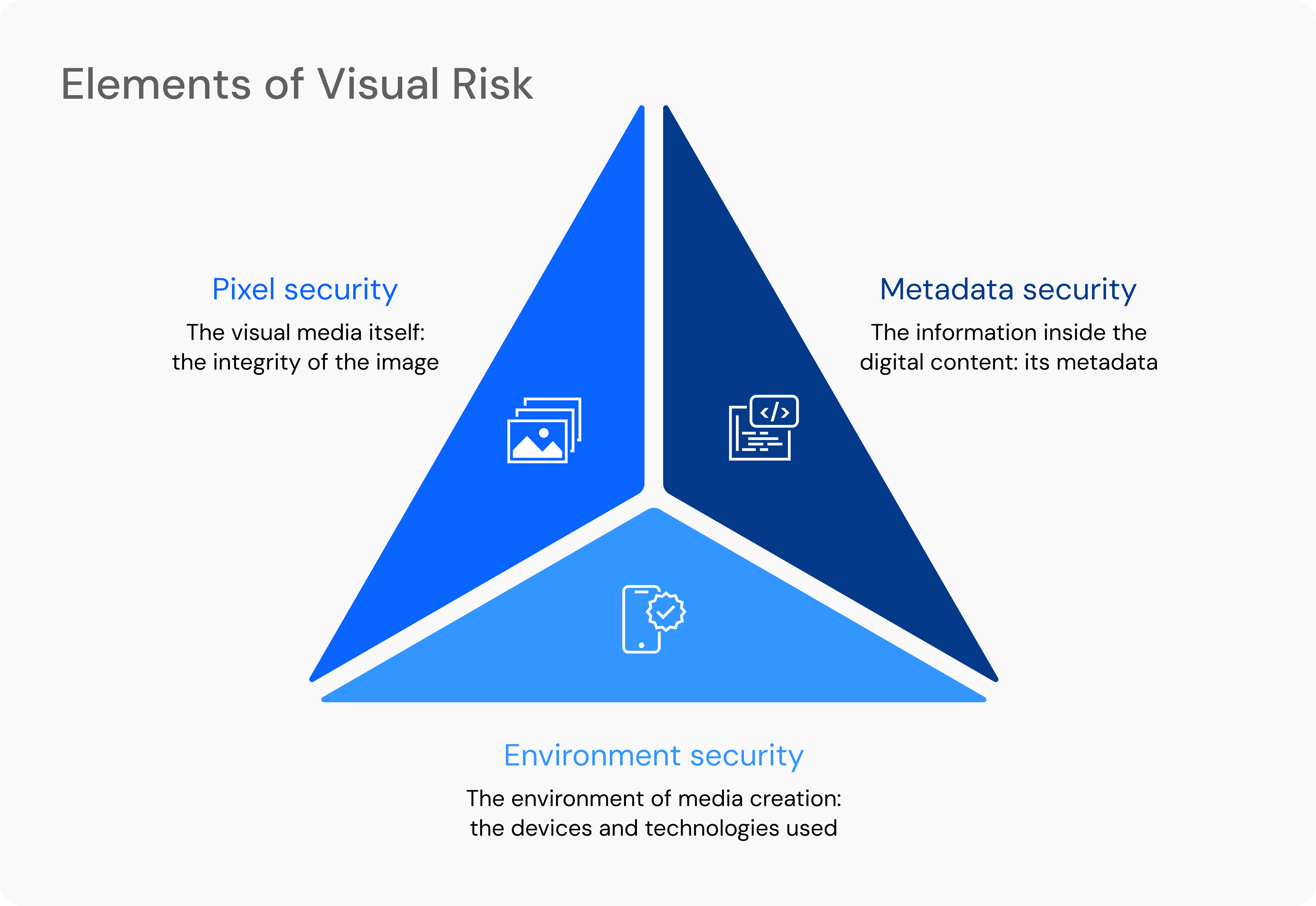
Visual risk is not just a fake or deceptive image, which is not new. It's much deeper than that, the risk within digital visual content is far greater than simply a fraudulent image. Mitigating visual risk has three critical considerations:
- The visual media itself: the integrity of the image (pixel security)
- The information inside the digital content: its metadata (metadata security)
- The environment of media creation: the devices and technologies used to create (environment security)
Not your normal risk
Unlike traditional cybersecurity categories or prominent threat vectors, such as phishing, hacks, or ransomware, digital visual risk is a bit more subtle. The risk manifests itself through slight changes or manipulations to otherwise frictionless processes that can be easily overlooked, dismissed as innocuous, or unnoticed altogether. However, changes to pixels, metadata, or the devices and environments used to create the content can have profound consequences for businesses today.
It's essential for businesses to consider the inherent risks associated with digital visuals. The consideration should not just be whether the image is real or fake, but also if the data and technology associated with that content are accurate and secure. One of the easiest ways to commit fraud is to simply reuse or recycle an actual image instead of creating a fake one, which can mislead the content consumer making a decision on that visual. Without establishing an environment to help mitigate all avenues of digital visual risks, it will be increasingly challenging to digitize any process, regardless of the speed or efficiency gains.
Pillars of visual risk
1. Integrity of visuals (pixel security)

This is often the fundamental question today: “Is that picture real?” Are the pixels we see genuinely and authentically captured without manipulation or alteration? Further, and something that would have seemed almost unimaginable only a few years ago, we must now also ask: were those pixels created by actual light and photons striking a camera sensor, or were they generated synthetically by artificial intelligence?
A few years ago we saw this challenge emerge with the advancements in hyper-realism, such as the “Pope in a puffy coat,” in which the late Pope Francis was depicted wearing a puffy white Balenciaga coat. Today we watch the deluge of videos from Sora 2 in almost disbelief. The realism of synthetically generated content is so powerful that it forces the question: “Is this real?”
No detection technology can distinguish authenticity from synthetic generation in real time, at scale, and with unquestionable accuracy. Further, provenance standards such as the C2PA or watermarks like SynthID can help mark AI, but are often stripped or lost as images move across the internet. In short, there is no foolproof way to identify AI or even cheapfakes (non-AI manipulations) online.
The only way to guarantee pixel authenticity and originality is by securing the process in which photons are captured and recorded as digital files. In other words, not relying on detecting the AI, but rather imbuing or marking the authenticity in a secure capture experience. In an insurance claim example, this would require a policyholder to take a net-new picture of their car damage using a specialized camera app, rather than uploading a pre-existing one or perhaps an image they received elsewhere.
Rebroadcast attacks are another method of photo fraud to watch out for, even in controlled environments. Anyone can hold their camera in front of a computer screen or a printed picture to capture a new photo of a pre-existing image. What stops bad actors from capturing an image off a screen? Differentiating between two- and three-dimensional objects and searching for anomalies, such as Moiré patterns and other markers of screens, can help mitigate this issue. This type of fraud is behavioral (not a technical setting) and is directly attributed to the broader visual risk landscape that businesses must account for.
2. Veracity of information inside (metadata security)
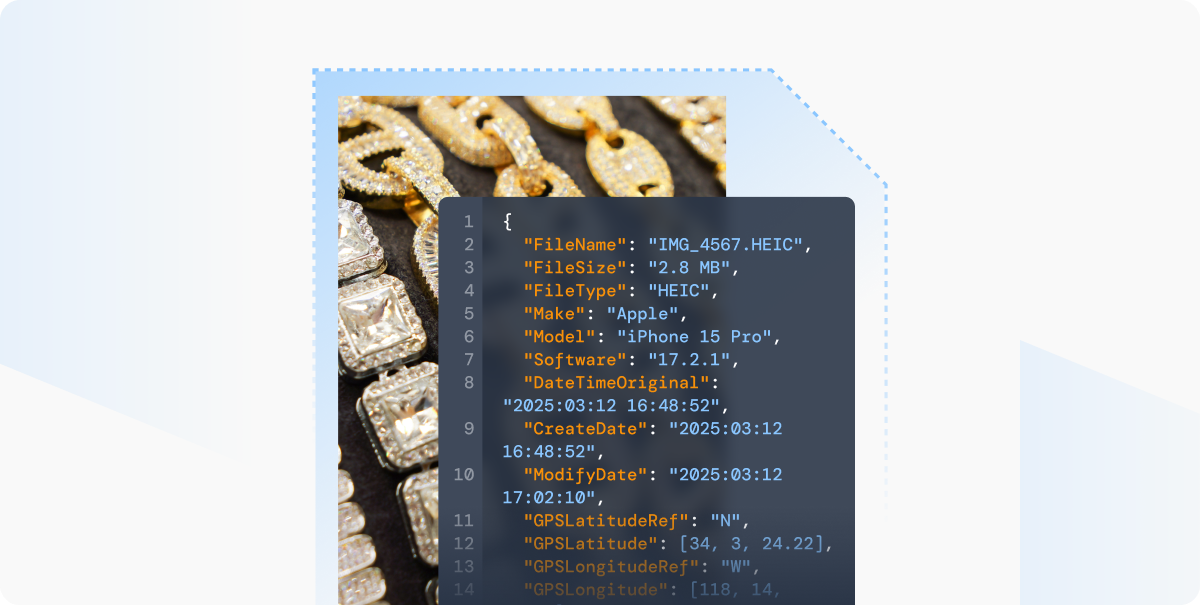
We’ve established that ensuring a controlled capture environment and checking for rebroadcast attacks is critical in mitigating visual risk. What about the metadata? One of the easiest ways to commit photo fraud is to falsify the metadata of an authentic digital image by altering its timestamp, date, or location.
How can metadata be modified? Sadly, it's much easier than it sounds. Hundreds of location-spoofing applications are readily available and easy to download. To make things more challenging, manufacturers have built in the ability to alter time/date/location directly from a smartphone’s photo gallery. On an iPhone, simply click on the information button on the image to immediately edit critical pieces of its metadata, like time, date and location. When the image is then sent to a recipient, they will see the altered information and have no way of knowing that the original metadata was manipulated.
Fraudsters frequently use these methods to deceive. For example, a bad actor underwriting a fake piece of jewelry could walk into a department store with a location-spoofing application and take a new image within an insurer’s application, disguising their location to appear as if they were home. The new image would prove possession of a high-ticket item at their residence for insurance underwriting and policy binding. Several months later, the item would magically be lost, allowing the bad actor to defraud the insurer with minimal effort.
Therefore, ensuring metadata accuracy is almost as critical as pixel security. How do we ensure metadata accuracy?
3. Environmental signals (device, technology, and behavioral security)

The final pillar of visual risk is the device and technology used to capture, process, transmit, and store visual information. Even if the pixels are authentic and the metadata appears accurate, the device itself can be compromised, which undermines everything associated with the digital content. Ensuring device and technology integrity is the first brick on which the entire visual risk mitigation framework rests.
Most assume that if an image comes from a smartphone, tablet, or connected camera, it can be trusted. Unfortunately, that assumption is dangerously outdated. Modern devices can be rooted, spoofed, or run with modified firmware that injects falsified data into the visual outputs. If the hardware or software capturing an image is not secured, no amount of verification can fully guarantee authenticity.
Organizations that rely on digital image capture must implement device attestation to ensure that only verified, uncompromised devices can capture and transmit imagery. This practice establishes a trusted foundation for visual data integrity from the very first point of interaction. Then, with verified data, critical information can be cryptographically sealed and aligned to an interoperable standard like the C2PA.
Securing the creation environment is challenging and there are other considerations beyond just the capture, notably the transmission layer. Once a visual asset leaves the device, whether uploaded through a mobile app, shared, or stored in the cloud, it becomes vulnerable to interception or alteration. Man-in-the-middle attacks, insecure APIs, or weak protocols can all introduce tampering without detection. Businesses should implement robust safeguards, ensuring state-of-the-art encryption and secure data transmission across every stage of their systems.
Considering the future
Visual risk management must be approached as a complete system, accounting for every layer of digital content integrity. This includes the pixels that make up an image, the metadata that defines it, and the devices and technologies that capture and transmit it. Business leaders should ensure they rely on safeguards and authentication across all three areas of visual risk.
Equally important is building understanding across teams. Teams need to be trained to recognize where visual risks can occur in their operations and pipeline, and how their tools and workflows depend on trustworthy digital content. By developing awareness and best practices, organizations can close gaps, reduce exposure, and strengthen confidence in the visual media that powers their operations. In today’s digital world, managing visual risk is not just a technical issue; it is a strategic responsibility that protects and accelerates operations in the AI era.
Subscribe to Truepic updates
Stay up to date with our latest resources and articles.

